Businesses are always looking for ways to increase their security and to improve their authorization rates. With payment tokenization, they can do both. Learn more about the different types of tokenization, how it works and the benefits it can have on your business.
Examples of Payment Tokenization
What Is Payment Tokenization?
As eCommerce continues to grow, payment tokenization is increasingly the technology of choice for keeping payment data secure, improving authorization rates and reducing costs. Payment tokenization is the process of replacing sensitive payment data, such as the primary account numbers (PAN) of a debit or credit card, with a unique digital identifier, called a token.
Using this token in place of the actual data during a transaction greatly reduces the risk of that data being compromised. Even if the token is stolen, the data is useless to the thief outside the specific context it was intended for.
Tokenization vs. Encryption
Encryption is the classic means of protecting sensitive data by transforming information with an encryption key, which can then only be read with the correct decryption key.
Unlike tokenization, when encrypted data is transferred, the actual sensitive information is still transmitted, leaving it vulnerable to being intercepted, decrypted and stolen. And all encrypted files, no matter how sophisticated, are eventually decryptable.
Tokens, however, are functionally useless if copied or stolen. They act more like unique keys to get access to data, which payment service providers (PSPs) or issuing banks will not provide outside the intended specific context or approved vendor.
Tokenization and encryption can be used in tandem for heightened payment security. For example, the data stored within a token vault is often encrypted. As a security measure, encryption is preferable in cases where large volumes of data need to be transferred or recipients need immediate access. For payments, tokenization is quickly becoming the standard thanks to its many relevant benefits.
Benefits of Tokenization
Because the token acts only as a placeholder and does not actually store any sensitive data, it carries a few important advantages over traditional data security methods like encryption:
- Increased Security: Not actually transmitting data means less exposure of sensitive information and greater difficulty for bad actors to copy or steal data. Safely storing debit or credit card data enables repeat customers to check out quickly and securely, while allowing new customers to shop with confidence. Hosted payment fields will encrypt customer data for a more secure checkout, while one-time and multi-use tokens securely process shopper data.
- Reduced Scope for PCI Compliance: The less data that a merchant handles, the easier it is to achieve the PCI data security standard. Having easier ways of meeting compliance with data security requirements through tokenization turns into cost savings.
- Increased Authorization Rates: A Visa report shows that merchants can experience a 2.1% increase in authorization rates when using tokenization. This especially applies to network tokenization, because the bank is the entity that issues the token, the merchant is automatically known and trusted.
- Increased Conversions and Revenue: Because customer data is always up to date for all the payment methods on file, tokenization helps to prevent declines due to card expiration, loss or theft. This helps to streamline the process of recurring transactions to improve conversion rates and prevent any interruptions in revenue.
- Encouraging Repeat Customers: Tokenization helps generate customer loyalty through convenient one-click/zero-click payments that provide a quick and secure checkout experience for shoppers. Tokenization can also match unique customer identifiers when customers shop anonymously. This makes it easier to track customers every time they shop, improving analytics to inform the creation of personalized customer experiences.
- Future Convenience: As tokenization technology continues to develop, merchants and their customers can look forward to other conveniences in the future. For example:
- Tokenization can be applied to omnichannel purchases, both online and in-person, enhancing a customer’s cross-channel experience.
- Eventually card PANs will be usable only as a reference for tokenized transactions – so the fear of having a customer’s PAN get out and be used to compromise their account will become obsolete.
How Does Tokenization Work?
Tokenization uses software to algorithmically generate a unique string of numbers — a token — to represent the sensitive data. This token is issued in real time and then passed through the internet or over a wireless network, where it can only be used with that one specific merchant or a specific type of purchase. The actual sensitive data, in this case the bank account number, remains securely stored within a token vault.
This process prevents the transmission of the sensitive data over a network, which means it cannot be intercepted by hackers or data thieves. Because the token is only useful for that one specific transaction, any attempt to copy and reuse the token will be futile.
Standard Debit and Credit Card Tokenization
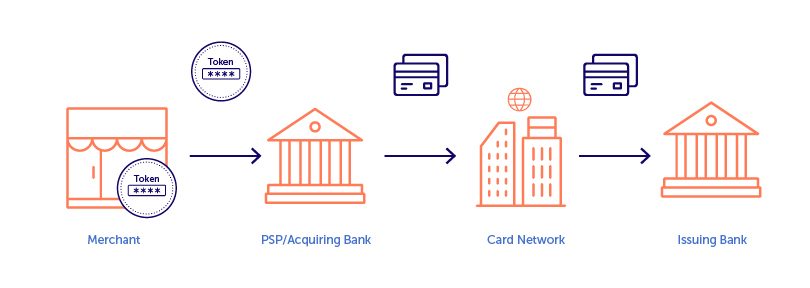
For credit and debit cards, the PAN is replaced with randomly generated numbers delivered by the PSP or acquiring bank, and then is passed over the network to complete the purchase.
As a result, sensitive bank and account information are not exposed, and instead are held in a secure token vault accessible only by the intended token holder. However, with simple payment tokens, the token is only used for the first part of the transaction on the merchant’s side. A card’s issuing bank does not have visibility into the tokens used by the PSP.
Network Tokenization
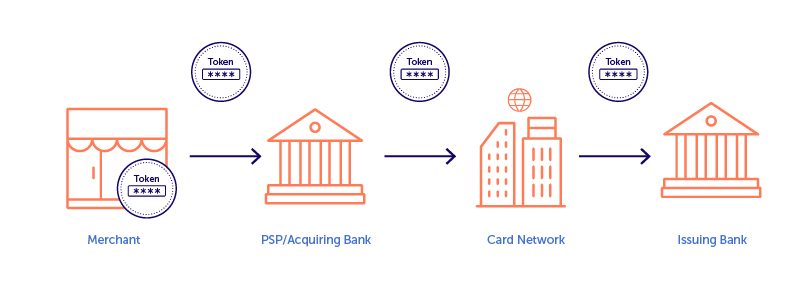
Network tokenization is a more recent advancement, where the issuing bank replaces the sensitive data of a customer’s account with a token unique to the application or platform where it is being used. Since network tokens are created by the issuer, they can be passed through the entire process. Network tokenization gives the customer greater confidence that their tokenized data is protected, and it increases the likelihood of transactions being approved by the issuing bank, as they have issued the token.
Examples of Payment Tokenization
When a customer is checking out, their data is encrypted to allow for secure checkout. Then, when the customer submits the checkout form, the sensitive card data is bound to a token, allowing the payments to be easily processed and the shopper details to be saved by including the token in an API request for future convenience.
Here are some everyday examples of payment tokenization in action:
- A customer purchases for the first time on a merchant’s site. The payment is processed and the customer’s details are saved on file as the token is included within the API request. For any future purchases this customer makes on the site, all personal information is saved and doesn’t need to be re-entered – making future purchases faster and more convenient.
- A merchant suffers a data breach from a malicious hacker attempting to access account and payment information. Thanks to network tokenization, every transaction was assigned a unique network token associated through an issuing bank and is specific only to those transactions. The merchant doesn’t have to worry about the randomized data being exploited as it does not contain actual payment information – protecting both the merchant’s customers and its reputation.
- A shopper makes a payment at a coffee shop with a mobile wallet from a smartphone application. The shopper’s debit or credit card information is replaced with a token, so there’s no risk of exposing the actual card information to hackers. Later, that shopper goes to the coffee shop’s website to purchase a gift card and the payment token is automatically recognized. The shopper receives an instant update on their loyalty points and can continue to make NFC mobile payments online or in-person without worrying about having sensitive payment data intercepted or stolen.
Tokenization is opening new possibilities for payment processing, and at BlueSnap we’re implementing both one-time and multi-use tokens to securely process shopper data. We use tokenization in combination with our Intelligent Payment Routing, securely sending transactions so that they are most likely to get approved, helping businesses to increase sales.
With BlueSnap’s Payment Orchestration Platform, you can save payment information using the Vaulted Shopper feature, which creates an additional token for future customer purchases. Contact us to request a free consultation on the benefits of payment tokenization and how it can directly benefit your business.
Payment Tokenization FAQs
- Is a network token reversible?
No, it is not. Unlike the encryption process, which can be reversed, there’s nothing to reverse in a token. It only works as a one-way key to provide access to a specific card or account and will not be recognized outside its specific intended context.
- How are tokens generated?
To generate a payment token, a number is created that is uniquely linked to that account. While standard tokens are generated algorithmically at the point of sale for a transaction, network generation is where an issuing bank generates a token and associates it with a specific account.
- Does using tokenization make me PCI compliant?
It may not automatically make your transactions compliant, but it can help to reduce your PCI burden as there’s no sensitive payment data being exchanged or stored.
- When do I need to worry about tokenization?
Sooner rather than later. You don’t want the burden or risk of storing card information, but you do want to cater to recurring shoppers. Having tokens for cards makes it easier for your customers to shop with you and keeps every transaction secure.
- What are the differences between simple tokens and network tokens?
Simple tokens are generated by a payment processor and, therefore, are unique to the processor that generated the token. Because network tokens are generated by the issuing bank, network tokens can work with any payment processor.
Related Resources:
- 5 Ways to Improve Your Debit and Credit Card Authorization Rates
- Achieving Payments Compliance: Everything You Need to Know
- Time for a New Payment Processor? [Quiz]
Frequently Asked Questions
What is payment tokenization?
Payment tokenization is the process of replacing sensitive payment data online (or digitally), such as the primary account numbers (PAN) of a credit card, with a placeholder token. Using this token in place of the actual data during a transaction greatly reduces the risk of that data being compromised. Even if it’s stolen, the data is useless to the thief outside of the specific context it was intended for.
What is the difference between tokenization and encryption?
Encryption is the classic means of protecting sensitive data by transforming information with an encryption key, which can then only be read with the correct decryption key. Unlike tokenization, when encrypted data is transferred, the actual sensitive information is still transmitted, leaving it vulnerable to being intercepted and stolen. And all encrypted files, no matter how sophisticated, are eventually decryptable.
Tokens, however, are functionally useless if copied or stolen. They act more like unique keys to get access to data, which issuing banks will not provide outside the intended specific context or approved vendor.
Does using payment tokenization make me PCI compliant?
Payment tokenization may not automatically make your transactions compliant, but it can reduce your PCI burden and thereby increase authorization rates.
How do digital payments work?
Whether for B2B card processing or B2C card transactions, digital payments work the same:
- The gateway captures the transaction request and either encrypts or tokenizes the information, then routes it to an acquiring bank.
- The acquiring bank (which provides your merchant account) takes ownership of the transaction request. Its job is to get authorization for the transaction.
- The issuing bank assesses the request: Does the customer have sufficient credit or funds? The issuing bank generates a response — yes or no — and sends it back to the acquiring bank via the card network.
- The acquiring bank sends the response back to the payment gateway.
- The payment gateway’s final job is to present the answer either back to the merchant or to the shopper directly (if you’re using a hosted payment page).
Congratulations, your order is approved!
Do you support the Payment Request API?
Yes! BlueSnap supports the Payment Request API by securely capturing and tokenizing the shopper’s data obtained from the browser, which allows you to process payments using BlueSnap’s Payment API while keeping your PCI compliance to a minimum. For complete details, refer to the Payment Request API (W3C) guide in the Developer Hub.


